Update: CareerBuilder says the issue with infected emails has been resolved and is not an ongoing problem. In an email this morning (5/15), a spokeswoman said, “The attack has been addressed, affected customers were notified right away and no other incidents have occurred.”
If you are a CareerBuilder customer, be careful what resumes you open. It could be malware. Or worse.
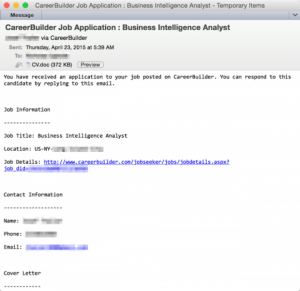
For the last few weeks, attackers have been sending CareerBuilder customers malicious attachments disguised as resume documents in response to their online job postings. Because they appear to be trustworthy and come through the job site’s mail platform, unwitting recruiters open the document and even forward the emails to hiring managers and others, unleashing a bit of code that then automatically downloads the malware. Once that happens, the program can steal data or wreak other havoc.
According to Proofpoint, a cybersecurity firm that first detected the phony emails, “The actor appeared to target positions in engineering and finance, such as ‘business analyst,’ ‘web developer,’ and ‘middleware developer’: the skills listed for these positions can reveal valuable information about the tools and software that is running in the target organization and thus enable the actor to tailor their attack.”
 A CareerBuilder spokeswoman said the job board is aware of the problem and has taken steps to limit the attack.
A CareerBuilder spokeswoman said the job board is aware of the problem and has taken steps to limit the attack.
“CareerBuilder is aware and has been investigating the situation.” the spokeswoman said. “CareerBuilder follows Incident Response protocols, investigating the scope and type of attack with the help of third party experts kept under contract, and sharing information with affected customers. CareerBuilder has controls in place to stop mass distribution of applications to job postings and takes a variety of preventative measures. ”
The company declined to go into specifics for security reasons. It also didn’t say how many, if any customers had become infected.
